What is the Centralized Audit Log feature and who should use it?
The Centralized Audit Log is a core Hoop platform feature designed to track every action taken within your environment. This includes actions by human users, automations, integrations, and AI components. It provides complete transparency and accountability for all activities.
This feature is essential for any regulated team or business that requires strict internal controls and comprehensive oversight of their data environment. It is crucial for security, legal, and compliance teams who need to investigate issues, prove adherence to governance policies, and quickly restore control after misconfigurations or errors. It serves as a unified audit trail for maximum control.
How does the Centralized Audit Log work to ensure compliance?
The system operates by logging specific events across various aspects of the Hoop platform. It unifies logs for easy investigation and ensures that all changes are traceable. You can filter the data by user, event, object, or specific time range, allowing you to drill into root causes efficiently. This detailed logging makes proving compliance straightforward.
Key logged events include:
- Authentication and session events.
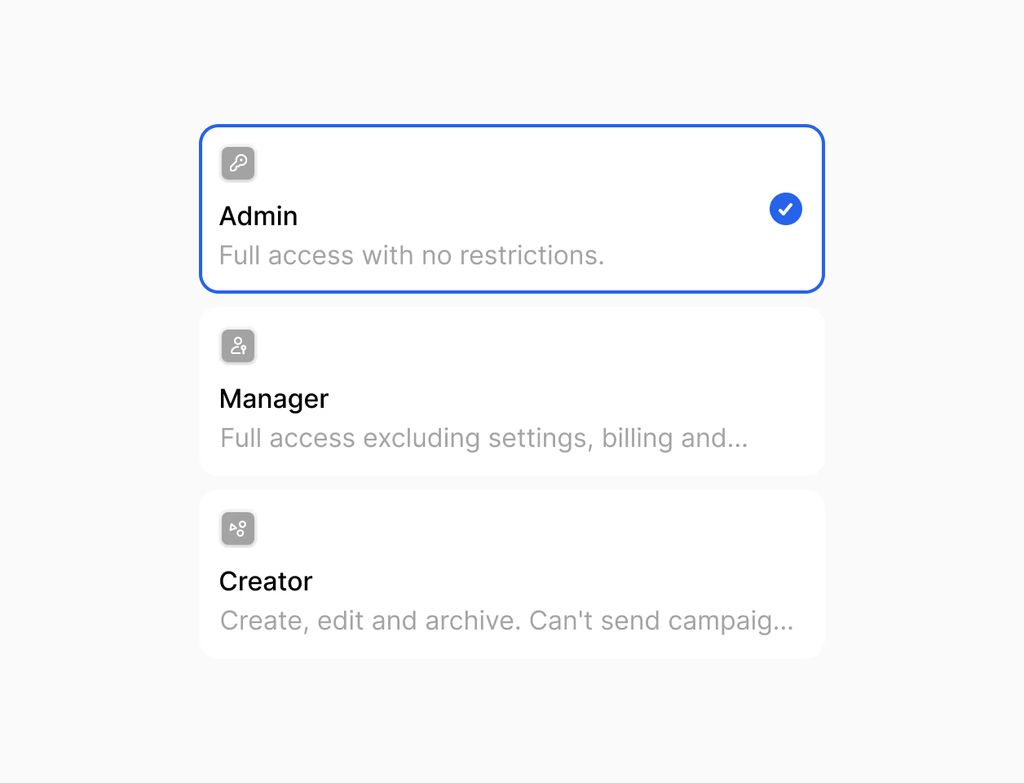
- Role, team, and partition changes.
- Workflow, property, and pipeline edits.
- App installs, scopes, and removals.
These detailed logs are retained and managed according to your governance policy, providing a continuous record for auditors.
What are the pricing plans associated with the Centralized Audit Log?
The Centralized Audit Log is available across multiple pricing tiers within the Hoop platform, ensuring accessibility for growing businesses and enterprises alike. This feature is included in the core, pro, and enterprise plans.
The specific access and retention limits may scale based on your subscription level. For example, higher-tier plans like Enterprise typically offer enhanced features like longer data retention controls and more advanced scoped filtering options to meet rigorous regulatory demands. Consult your plan details to understand the full capabilities available to your organization.
What options are available for investigating and sharing audit data?
The Centralized Audit Log is built to make investigation fast and efficient. You have access to scoped filtering tools that let you isolate activity by users, teams, or specific objects to quickly find the root cause of an issue. The filtering capabilities simplify the process of reviewing complex activity logs.
When an investigation is complete, you can easily export filtered log results. This allows you to share critical evidence quickly with various stakeholders:
- Security teams for incident response.
- Legal departments for discovery.
- External auditors for compliance reporting.
The ability to share evidence in seconds streamlines the entire governance and security process within Hoop.
How is data security and access handled within the audit log?
Security and data handling are prioritized within the Centralized Audit Log. Access to the raw log data is strictly limited to authorized administrators based on their assigned role and the organization's current plan. This ensures that only personnel with the proper security clearances can view sensitive activity data.
The logs themselves support internal controls with full traceability across configuration, data access, and integration endpoints. Furthermore, administrators can actively monitor high-risk actions using saved views and set up alerts. This proactive monitoring allows teams to react before potential security issues impact customers or compromise data quality in the Hoop environment.
Does the Centralized Audit Log track activity across connected integrations?
Yes, the Centralized Audit Log tracks activity related to integrations to provide a holistic view of your environment. This is crucial because modern workflows often rely on third-party applications, and any changes made through these endpoints must be monitored for compliance and security purposes.
The logs specifically capture events like:
- App installations and removals.
- Changes to app scopes and permissions.
- Activity and changes initiated by the integrations themselves.
By including integrations, the audit log ensures continuous traceability across all configuration and data access points, providing a unified and comprehensive security record across the entire Hoop platform ecosystem.